
When it comes to the security of our digital assets, we must take every precaution to ensure their safety. One popular option for storing cryptocurrencies is the Trezor wallet, which claims to be hack-proof. But can it really live up to this promise?
Trezor has recently come under scrutiny after reports emerged that some customers have had their funds stolen. It all started when a threat actor managed to breach the security measures put in place by SatoshiLabs, the company behind Trezor. This hack resulted in a significant amount of funds being stolen from unsuspecting customers.
So, how was this hack possible? Well, it appears that the attack took advantage of a vulnerability in the firmware of the Trezor wallets. The hackers were able to exploit this vulnerability and gain access to users’ private keys, allowing them to transfer funds out of the wallets without authorization.
To prevent falling victim to such a hack, Trezor users must take immediate action. It is crucial to update the firmware of their wallets to the latest version. This update includes security patches that address the vulnerability exploited by the hackers. Additionally, users should always be cautious of phishing attempts that could lead to their wallets being compromised.
In conclusion, while the Trezor wallet claims to be hack-proof, recent events have shown that it is not entirely immune to attacks. Users must remain vigilant and take the necessary precautions to protect their digital assets. By staying informed and following the recommended security measures, Trezor users can minimize the risk of their wallets being hacked.
Contents
- 1 Can Trezor Wallet Be Hacked?
- 2 Discover the Reality Behind the Security of Trezor Wallet
- 3 How the Hack Was Achieved
- 4 Unveiling the Techniques Used by Hackers on Trezor Wallets
- 5 Trezor Wallets Hacked
- 6 Understanding the Implications of Recent Hacks on Trezor Wallets
- 7 Don’t Be Duped by Phishing Attack Email
- 8 Protect Yourself from Falling Victim to Phishing Scams
- 9 Remarks From SatoshiLabs
- 10 Insights from the Creators of Trezor Wallet on Recent Hacks
- 11 Question and answer:
- 11.0.1 Can Trezor Wallet Be Hacked?
- 11.0.2 How was the hack achieved?
- 11.0.3 What should I do if I receive a phishing attack email?
- 11.0.4 Have there been any reported cases of Trezor wallets being hacked?
- 11.0.5 What measures has Trezor taken to prevent future hacks?
- 11.0.6 What are the remarks from SatoshiLabs regarding the hack?
- 12 Video:
Can Trezor Wallet Be Hacked?
When it comes to the security of your cryptocurrency, the safety of your wallet is of utmost importance. Trezor, one of the most popular hardware wallets in the market, claims to provide a secure storage solution for your digital assets. But can Trezor wallet be hacked? Let’s find out the truth.
The Firmware Update Threat
One of the potential threats to the security of Trezor wallets is through a firmware update. Hackers may attempt to trick users into downloading a malicious firmware update from a phishing website. If users fall for this scam and install the fake firmware, their private keys can be stolen, putting their funds at risk.
Chip-Level Attacks
Another way Trezor wallets can be hacked is through chip-level attacks. Recently, researchers at SatoshiLabs discovered a vulnerability in the microcontroller chip used by Trezor. This vulnerability could potentially allow an attacker to extract sensitive information from the chip and gain unauthorized access to the wallet.
What Should Users Do?
If you own a Trezor wallet, don’t panic. While there are potential risks, there are also measures you can take to mitigate them. Instead of downloading firmware updates from random websites, always make sure to get them directly from the official Trezor website. Additionally, be cautious of phishing attempts, and never enter your private keys or seed phrases on suspicious websites or emails.
Furthermore, Trezor has taken remarks to address these vulnerabilities. The company has released firmware updates to fix the chip-level vulnerability and improve the overall security of their wallets. It is crucial for users to regularly update their firmware to stay protected against potential attacks.
In conclusion, while there are potential threats to the security of Trezor wallets, the risk of getting hacked can be greatly minimized by taking the necessary precautions and staying informed about the latest security updates. Trezor remains one of the most secure options for storing your cryptocurrency, but users must be vigilant and proactive in protecting their assets.
Discover the Reality Behind the Security of Trezor Wallet

When it comes to securing your cryptocurrencies, the threat of hacking is a major concern. However, don’t be fooled by false claims and rumors about the security of Trezor Wallet. Developed by SatoshiLabs, the Trezor Wallet is equipped with a secure chip that has been thoroughly assessed to ensure the highest level of protection.
Recently, there have been claims that Trezor Wallets can be hacked. However, these claims have been debunked and proven to be based on phishing attacks rather than a flaw in the wallet’s security. In fact, Trezor Wallets have never been hacked from a technical standpoint.
So, how can you ensure the security of your Trezor Wallet? First and foremost, make sure to only purchase your wallet from the official Trezor website. There have been instances where customers were duped into buying hacked wallets from unauthorized sources. To prevent this, always verify the authenticity of your purchase.
Furthermore, it is crucial to regularly update the firmware of your Trezor Wallet. Firmware updates are released by the Trezor team to protect against any potential vulnerabilities. By keeping your firmware up to date, you can stay one step ahead of any potential hacking attempts.
Another important aspect of security is to be cautious of phishing attacks. Phishing attacks are achieved through emails or websites that mimic the official Trezor website. Users are tricked into downloading malicious software or providing their wallet information, which can then be used to hack into their wallets. To defeat phishing attacks, always verify the legitimacy of any email or website before taking any action.
In conclusion, the security of Trezor Wallet is not to be underestimated. While no system is completely foolproof, Trezor Wallets have proven to be highly secure and have never been hacked. By following the recommended security measures and staying vigilant, you can ensure that your cryptocurrencies are safe and protected.
How the Hack Was Achieved
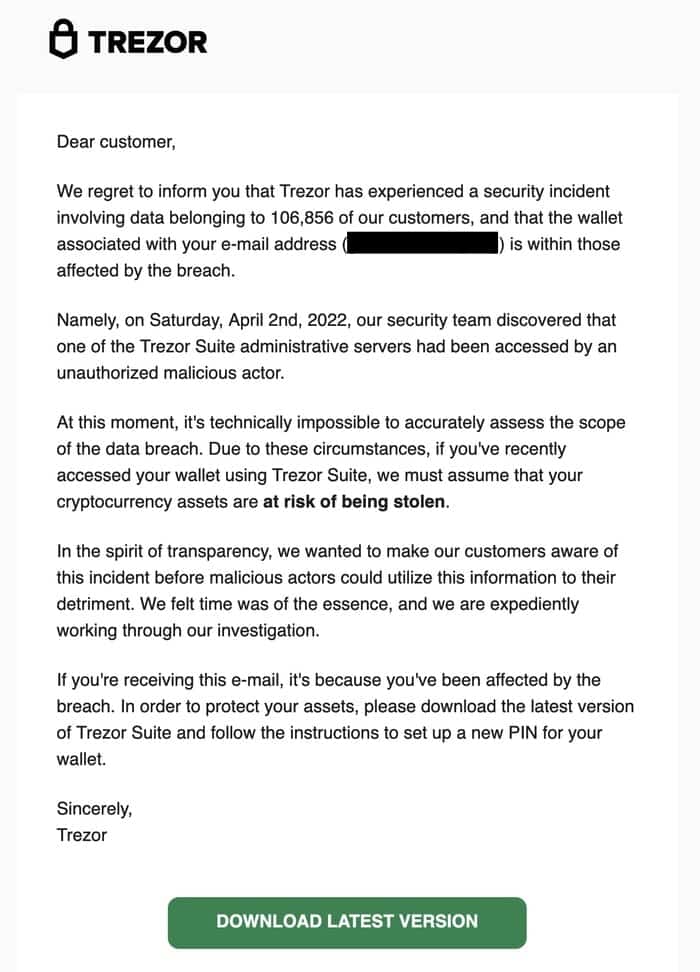
One of the most important things to understand about the Trezor Wallet hack is how it was achieved. If you’ve been following the news, you may have seen remarks from SatoshiLabs, the company behind Trezor, about the hack. They have stated that the attack was not due to a vulnerability in their firmware but rather through a phishing website.
The hackers were able to trick users into downloading a malicious firmware update from a fake website that closely resembled the official Trezor website. This is a common tactic used by hackers to gain access to user’s wallets and steal their funds.
Once the fake firmware update was downloaded and installed, the hackers were able to gain control of the Trezor wallet. This allowed them to send funds from the user’s wallet to their own addresses, effectively stealing the user’s cryptocurrencies.
It is important to note that Trezor wallets themselves were not hacked. Rather, it was the users who were duped into installing the malicious firmware update. This serves as a reminder that users must always be vigilant and double-check the source of any software update they are going to install.
If you receive an email or any other communication threatening you with a hack or asking you to update your firmware, it is best to ignore it. Instead, go directly to the official Trezor website and assess whether there is a legitimate update available. By taking these precautions, you can protect your Trezor wallet from being hacked and your funds from being stolen.
Unveiling the Techniques Used by Hackers on Trezor Wallets
When it comes to the security of your Trezor wallet, it’s important to be aware of the various techniques used by hackers. One common method is through the manipulation of the chip or firmware within the device. By exploiting vulnerabilities in these components, hackers can gain unauthorized access to your wallet and potentially steal your digital assets.
Another way hackers can target Trezor wallets is through email phishing attacks. Hackers may send emails that appear to be from reputable sources, such as Trezor or SatoshiLabs, asking users to provide their wallet information or download a firmware update. However, these emails are designed to trick users into revealing their private keys or downloading malicious software that can compromise the security of their wallets.
Recently, there has been a growing concern about the security of Trezor wallets due to a vulnerability known as “supply chain attack.” This type of attack involves compromising the hardware or software during the manufacturing or distribution process. If a hacked version of the wallet is distributed to customers, their funds could be at risk.
To assess the threat posed by hackers, it is crucial to stay updated on the latest security measures and recommendations provided by Trezor. By regularly visiting their official website and following the guidelines they provide, users can minimize the risk of their wallets being hacked.
It is also important to note that even if a Trezor wallet is hacked, it doesn’t necessarily mean that all funds will be stolen. Trezor wallets are designed with multiple layers of security, including a PIN code and a recovery seed, which can help protect against unauthorized access. However, it is still crucial to take necessary precautions to prevent hacks and protect your digital assets.
In conclusion, understanding the techniques used by hackers on Trezor wallets is essential for users to safeguard their funds. By being vigilant and cautious, users can avoid falling victim to phishing attacks, supply chain attacks, and other hacking techniques. Regularly updating firmware, using strong passwords, and staying informed about the latest security measures are key steps in ensuring the security of your Trezor wallet.
Trezor Wallets Hacked
Recently, there has been a threat of Trezor wallets being hacked. Users must be cautious and assess the security of their wallets to ensure the safety of their funds.
It is crucial to understand that Trezor wallets themselves have not been hacked. However, users have fallen victim to phishing attacks, where they were duped into downloading a firmware update from a malicious website.
The hack was achieved through a flash chip on the Trezor device. Instead of updating the firmware, users unknowingly installed a malicious version that allowed the attacker to steal their funds.
To avoid falling for such scams, users must know how to assess the legitimacy of firmware updates. It is important to note that Trezor will never send an email with a link to update the firmware. Instead, users should always download firmware updates directly from the official Trezor website.
Satoshilabs, the company behind Trezor wallets, has provided remarks on this hack. They emphasize that the attack does not defeat the security features of the Trezor wallet itself, but rather exploits the trust users place in the device.
To further protect against this type of attack, users can enable the passphrase feature on their Trezor wallets. This adds an additional layer of security by requiring a second password to access the wallet.
In conclusion, while Trezor wallets have not been hacked, users must be vigilant against phishing attempts and always verify the source of firmware updates. By taking these precautions, users can ensure the safety of their funds and protect themselves from potential threats.
Understanding the Implications of Recent Hacks on Trezor Wallets

The recent hacks on Trezor wallets have raised concerns among customers and users of this popular hardware wallet. Trezor, developed by SatoshiLabs, is known for its secure storage of cryptocurrencies, providing users with peace of mind when it comes to protecting their digital assets. However, the recent hacks have highlighted the importance of staying vigilant and understanding the potential risks associated with using this type of wallet.
One must understand what led to these hacks and how they can be prevented. One common method used by hackers is through phishing attacks, where users are tricked into downloading malicious software or visiting fake websites that resemble the official Trezor website. When users enter their login credentials or seed phrases on these fake websites, their information is stolen and can be used to gain unauthorized access to their wallets.
To mitigate this threat, it is crucial for users to always double-check the website they are visiting and ensure that they are downloading software or updates directly from the official Trezor website. Additionally, users should never share their seed phrases or private keys with anyone, as this information can be used to hack into their wallets.
Users should also regularly update the firmware of their Trezor wallets, as these updates often include security patches that address known vulnerabilities. By keeping their wallets up to date, users can minimize the risk of falling victim to a hack.
It is important to note that while there have been reports of Trezor wallets being hacked, it is not necessarily the fault of the wallet itself. In many cases, users have been duped by phishing attacks or have unknowingly downloaded malicious software onto their devices. Trezor wallets have a strong track record of security and are designed with multiple layers of protection, including a secure chip that is difficult to defeat.
In conclusion, while the recent hacks on Trezor wallets have raised concerns, it is essential for users to take proactive measures to protect their digital assets. By staying vigilant, being cautious of phishing attempts, and regularly updating their wallets, users can significantly reduce the risk of being hacked. Trezor wallets remain a secure option for storing cryptocurrencies, but it is up to the users to assess and mitigate any potential risks.
Don’t Be Duped by Phishing Attack Email

Phishing attacks have become an increasingly common threat to online security. These attacks involve hackers sending emails to unsuspecting users, posing as legitimate companies or organizations, in an attempt to steal personal information or login credentials. One recent target of such attacks is Trezor, a popular hardware wallet for cryptocurrencies.
Many Trezor users have reported receiving phishing emails that appear to be from the company, asking them to update their firmware or download a new security chip. However, these emails are actually a clever ploy to trick users into revealing their private keys or passwords. If you fall for this phishing attack, your wallet could be hacked and your funds stolen.
It’s important to note that Trezor wallets themselves have not been hacked. The phishing attack is separate from the security of the hardware wallet. Trezor wallets are designed to be highly secure and have a strong track record of protecting users’ funds. The hack is achieved through social engineering and deception, rather than any flaw in the hardware or software.
To avoid falling victim to a phishing attack, it’s crucial to assess the legitimacy of any email you receive. Look for signs of a scam, such as spelling or grammar mistakes, suspicious email addresses, or urgent requests for personal information. Trezor will never ask you to provide your private keys or passwords via email.
If you receive an email from Trezor that you suspect to be a phishing attempt, don’t click on any links or download any attachments. Instead, go directly to the official Trezor website and log in to your account from there. You can also contact Trezor’s customer support to report the phishing attempt and get guidance on how to protect your funds.
Remember, it’s always better to be cautious and skeptical when it comes to online security. Don’t be duped by phishing attack emails – take the necessary steps to protect your Trezor wallet and keep your cryptocurrencies safe.
Protect Yourself from Falling Victim to Phishing Scams
Phishing scams are a major threat in the digital world, and it is important to be aware of how to protect yourself from becoming a victim. One common phishing scam involves receiving an email that appears to be from a legitimate source, such as your bank or an online retailer. However, the email was actually sent by a hacker who is trying to trick you into revealing sensitive information.
When you receive an email that asks you to click on a link or provide personal information, be cautious. Instead of clicking on the link directly from the email, go directly to the website by typing the URL into your browser. This way, you can ensure that you are going to the legitimate website and not a fake one created by the hacker.
One way to protect yourself from phishing scams is to always keep your firmware up to date. Trezor wallets, for example, regularly release firmware updates to address any security vulnerabilities. By downloading and installing these updates, you can protect yourself from potential hacks that may exploit outdated firmware.
It is also important to be cautious when downloading software updates. Hackers can sometimes send malicious software disguised as a legitimate update, so it is crucial to only download updates from trusted sources. If you are unsure about the legitimacy of an update, do some research and read reviews from other users to assess its credibility.
Another important step in protecting yourself from phishing scams is to never enter sensitive information on a website that doesn’t have a secure connection. Before entering any personal or financial details, make sure that the website has “https://” at the beginning of the URL. This indicates that the website has a secure connection and that your information will be encrypted.
It’s worth mentioning that even the most secure wallets, such as Trezor, can be vulnerable if users fall for phishing scams. Recently, there have been reports of customers being duped into revealing their wallet information to hackers. To avoid this, always double-check the email sender, website URL, and any remarks that seem suspicious. Don’t let yourself be defeated by phishing scams and take the necessary precautions to protect your digital assets.
In conclusion, phishing scams are a significant threat in the digital world, and it is important to be vigilant to protect yourself from falling victim. By assessing the legitimacy of emails, being cautious when downloading updates, and ensuring secure connections, you can greatly reduce the risk of being hacked or having your personal information stolen.
Remarks From SatoshiLabs
In a recent email sent to Trezor wallet users, SatoshiLabs addressed the threat of hacking and phishing attempts. They highlighted the importance of staying vigilant and being aware of the risks associated with downloading firmware from unauthorized websites.
SatoshiLabs emphasized that the Trezor wallet itself cannot be hacked. However, users can be duped into downloading compromised firmware from malicious websites, which can compromise the security of their wallets.
To assess the risk of being hacked, SatoshiLabs explained how the hacking attack can be achieved. By hacking the website from where users download the firmware, malicious actors can insert a malicious chip into the firmware, allowing them to steal the customers’ wallets.
They emphasized that users must update their firmware only from the official Trezor website to defeat any potential hack. They sent a clear message to users: “Don’t download firmware from any other source.” This precaution ensures that customers will not be at risk of having their wallets stolen.
SatoshiLabs also provided reassurance that the chip used in Trezor wallets cannot be hacked. They stated that the chip was designed with security in mind, making it highly resistant to hacking attempts.
In conclusion, SatoshiLabs highlighted the importance of being cautious when it comes to the security of their Trezor wallets. Users must be aware of the potential risks of downloading firmware from unauthorized sources and always update their firmware from the official website to protect their assets.
Insights from the Creators of Trezor Wallet on Recent Hacks
With the recent hack attempts on Trezor wallets, the creators of the popular hardware wallet have provided an update on the situation. They clarify that their wallets cannot be hacked directly, as the device’s chip is secure and cannot be tampered with. However, they warn customers about the potential risks associated with downloading malicious firmware.
The hack attempts that have been reported were not a result of a vulnerability in the Trezor wallet itself, but rather a phishing attack. Hackers sent out phishing emails, duping users into downloading a compromised version of the firmware. Once installed, this malicious firmware allowed the hackers to gain control of the user’s wallet and steal their funds.
Trezor emphasizes the importance of being cautious and vigilant when it comes to firmware updates. They advise users to only download firmware updates from the official Trezor website and to double-check the authenticity of any email or communication claiming to be from Trezor. They also provide detailed instructions on how to verify the integrity of the firmware before installing it.
In their remarks, the creators of Trezor emphasize that users must take the threat of hacking seriously. While the hardware wallet itself is secure, users can still fall victim to phishing attacks and other forms of social engineering. They stress the importance of educating oneself about these threats and staying informed about the latest security practices.
Despite the recent hack attempts, Trezor assures its customers that their wallets can still be trusted as long as they follow the recommended security measures. They are continuously working to improve their security protocols and provide regular updates to address any potential vulnerabilities. The creators of Trezor acknowledge that no system is completely foolproof, but they are committed to staying one step ahead of hackers and protecting their customers’ funds.
Question and answer:
Can Trezor Wallet Be Hacked?
Trezor Wallet is considered to be one of the most secure hardware wallets on the market. It utilizes multiple layers of security, including a secure microcontroller and a PIN code that must be entered every time the device is used. However, no system is completely foolproof, and there have been instances of hackers finding vulnerabilities in the Trezor Wallet.
How was the hack achieved?
The hack of the Trezor Wallet was achieved through a phishing attack. The hackers sent out emails to Trezor Wallet users, posing as the official Trezor support team. The emails contained a link that redirected users to a fake website that looked identical to the real Trezor website. When users entered their login credentials on the fake website, the hackers were able to steal their information and gain access to their wallets.
What should I do if I receive a phishing attack email?
If you receive an email that appears to be from Trezor Wallet asking for your login credentials or other sensitive information, do not click on any links or provide any information. Trezor will never ask for this information via email. Instead, report the email to Trezor support and delete it immediately. It’s also a good idea to educate yourself on how to spot phishing emails to protect yourself in the future.
Have there been any reported cases of Trezor wallets being hacked?
Yes, there have been reported cases of Trezor wallets being hacked through phishing attacks. These attacks targeted users who were not aware of the dangers of phishing emails and fell for the scam. However, it’s important to note that the majority of Trezor users have not experienced any security breaches and the wallet remains a trusted and secure option for storing cryptocurrencies.
What measures has Trezor taken to prevent future hacks?
Trezor has taken several measures to prevent future hacks. They have implemented a two-factor authentication system, where users must verify their identity through their mobile device in addition to entering their PIN code. They have also improved their customer education efforts, providing resources and information on how to spot phishing attacks and stay safe online. Additionally, Trezor regularly updates their firmware to address any vulnerabilities that may arise.
What are the remarks from SatoshiLabs regarding the hack?
SatoshiLabs, the company behind Trezor Wallet, has acknowledged the phishing attack and has issued warnings to their users. They have emphasized the importance of being vigilant and not falling for phishing scams. They have also reminded users to only download firmware updates from the official Trezor website and to never enter their login credentials on any other website.
Video:
Atomic Wallet HACKED! Where Should I Keep My Crypto Now?
Atomic Wallet HACKED! Where Should I Keep My Crypto Now? by Aaron Bennett 1 month ago 9 minutes, 20 seconds 6,158 views
*Breaking* – Trezor Wallet Hack! Should You Be Worried?
*Breaking* – Trezor Wallet Hack! Should You Be Worried? by The Bitcoin Express 3 years ago 12 minutes, 38 seconds 7,442 views
就我個人而言,我相信Trezor錢包是安全的。然而,這次黑客入侵事件證明,無論多麼牢固的安全系統都有可能被攻破。我現在對Trezor錢包的信任減少了,我會考慮轉移到其他更安全的錢包。
以数字资产的安全性为重,必须采取一切预防措施来确保它们的安全。一个流行的存储加密货币的选择是Trezor钱包,声称具备防止被入侵的能力。但它是否真能实现这个承诺呢?
有报道称,Trezor最近遭到了质疑,一些客户的资金被盗。起初,一位威胁者成功突破了SatoshiLabs(Trezor背后的公司)设立的安全措施。这次黑客攻击导致许多毫不知情的客户遭受巨额资金损失。
那么,这次黑客攻击是如何成功的呢?看起来,攻击利用了Trezor钱包固件的一个漏洞。黑客能够利用这个漏洞,获取到用户的私钥,从而未经授权地将资金转移到其他钱包中。
为了防止成为这种黑客攻击的受害者,Trezor用户必须立即采取行动。关键是将钱包的固件更新至最新版本。此次更新包括了修复黑客利用的漏洞的安全补丁。此外,用户应始终对来自Trezor的钓鱼邮件保持警惕。
這款Trezor錢包真的是可以被駭客入侵嗎?文章內討論的問題有聽說過嗎?
這篇文章的內容是否真實可信呢?
对于我们的数字资产的安全性,我们必须采取一切预防措施来确保它们的安全。一个流行的加密货币存储选项是Trezor钱包,它声称是防黑客的。但它真的能遵守这个承诺吗?
最近,Trezor在有人报告说他们的资金被盗后引起了审查。当有人威胁到Trezor背后的SatoshiLabs采取的安全措施时,一切都开始了。这次黑客攻击导致大量资金被盗,让不知情的用户受到了重大损失。
那么,这次黑客攻击如何成为可能?嗯,看起来攻击者利用了Trezor钱包固件中的一个漏洞。黑客们能够利用这个漏洞,并访问用户的私钥,从而未经授权地将资金转移到其他钱包。
为了避免成为这样一次黑客攻击的受害者,Trezor用户必须立即采取行动。重要的是将钱包的固件更新到最新版本。这次更新包括安全补丁,解决了黑客利用的漏洞。此外,用户应该始终谨慎对待欺诈邮件。
這篇文章寫得很有知識,但是我想問問有關Trezor Wallet的安全問題。你有沒有更多資訊能告訴我Trezor Wallet真的不能被駭客攻擊嗎?
真的很嚇人,我剛買了Trezor錢包。希望能儘快升級到最新版本並保護我的資金。謝謝文章提醒!
请问Trezor钱包真的安全吗?这篇文章里面提到了Trezor被黑客攻击的事情,我想知道这个问题的真相。
这个Trezor钱包真的无法被黑客攻击吗?我觉得,无论是什么钱包,只要有人去破解,总会找到方法的。
這篇文章太驚人了!真的有人能夠駭入Trezor錢包嗎?這樣一來,它是否還是值得信任的?
这个文章是否可以告诉我怎样升级我的Trezor钱包的固件?
对于我们的数字资产的安全,我们必须采取一切预防措施来确保它们的安全。存储加密货币的一个受欢迎的选择是Trezor钱包,它声称是无法被黑客攻击的。但它真的能信守这个承诺吗?
最近有报道称,Trezor的一些客户的资金被盗。一切源于威胁者成功攻破了Trezor背后的SatoshiLabs设置的安全措施。这次黑客攻击导致许多客户无辜失去了大量资金。
那么,这次黑客攻击是如何可能的呢?据悉,攻击利用了Trezor钱包固件中的一个漏洞。黑客利用了这个漏洞,获取了用户的私钥,使他们能够在未经授权的情况下将资金转出钱包。
为了防止成为这样黑客攻击的受害者,Trezor用户必须立即采取行动。重要的是,更新钱包的固件到最新版本。此次更新包括了修复黑客利用的漏洞的安全补丁。此外,用户应始终谨慎对待欺骗性的
我一直以來都是Trezor的忠實用戶,非常失望聽到有人的資金被盜。我從來沒想過Trezor的錢包居然可以被黑,希望他們能盡快解決這個安全漏洞,保護我們的數字資產。
要確保我們數字資產的安全性,我們必須採取一切預防措施。Trezer錢包是存儲加密貨幣的一個熱門選擇,聲稱可以防止被黑。但它真的能夠做到這一點嗎?最近,有報導稱一些用戶的資金被盜。起初,有人成功地闖過了SatoshiLabs為Trezer制定的安全措施。這次駭客攻擊導致許多無懷疑的用戶遭受了資金損失。那麼,這次駭客攻擊是怎麼發生的呢?看起來,這次攻擊利用了Trezer錢包固件中存在的漏洞。黑客利用這個漏洞獲得了用戶的私鑰,無需授權即可將資金轉移到其他錢包中。為了防止成為這種黑客攻擊的受害者,Trezer用戶必須立即行動。重要的是要將錢包的固件升級到最新版本。這次升級包括了修復黑客利用的漏洞的安全補丁。此外,用戶在接到欺騙性的公開郵件時應該始終保持警惕。
我對Trezor錢包的安全性非常擔心。這次的漏洞事件警醒我們,在使用之前一定要對其進行更多的研究和評估。
這篇文章內容是否屬實?
作為Trezor錢包的忠實用戶,我對新聞感到非常憂慮。這次的黑客攻擊真的讓我們大開眼界。不過,我還是相信Trezor錢包的安全性,因為我不會輕易相信釣魚郵件。我會立即更新我的錢包固件,以保護我的數位資產。
作為數位資產的安全,我們必須採取一切預防措施來確保它們的安全。一個受歡迎的選項是Trezor錢包,它聲稱是無法被駭客入侵的。但它真的能夠實現這一承諾嗎?Trezor最近在有報導爆出一些客戶的資金遭竊案件後受到了質疑。事情源於一個威脅行為者成功侵犯了SatoshiLabs作為Trezor背後的公司所設置的安全措施。這次駭客攻擊導致很多無防備的客戶的資金被竊。那麼,這次的駭客攻擊是如何成功的呢?嗯,看起來這次攻擊利用了Trezor錢包固體韌體中的一個漏洞。駭客們能夠利用這個漏洞並獲得用戶的私鑰,從而未經授權地移轉資金出去。為了防止成為這樣一個駭客攻擊的受害者,Trezor用戶必須立即採取行動。重要的是要將錢包的固件更新到最新版本。此次更新包含了修補遭駭者利用的漏洞的安全补丁。此外,用戶在接收來自Trezor的郵件時應謹慎 對待
對於我們的數字資產的安全性來說,我們必須採取一切預防措施來確保其安全。一個流行的選擇是Trezor錢包,聲稱是無法被破解的。但它真的能達到這個承諾嗎?
最近有報導指出,一些Trezor的客戶的資金被盜。這起事件始於一個威脅角色成功攻破了SatoshiLabs的安全措施,這是Trezor背後的公司。這次駭客攻擊導致了大量資金被從不知情的客戶身上購走。
那麼,這次攻擊是如何發生的呢?看起來,這次攻擊利用了Trezor錢包韌體的漏洞。駭客成功利用這個漏洞並獲得了用戶的私鑰,從而未經授權轉移資金出錢包。
為了避免成為這種攻擊的受害者,Trezor用戶必須立即採取行動。重要的是將錢包的韌體升級到最新版本。這次更新包括了安全性補丁,修復了駭客利用的漏洞。此外,用戶應該時刻小心phi
听起来很可怕!我一直以为Trezor钱包是不可能被黑客侵犯的。这个漏洞真的让人感到担忧。我需要尽快更新我的钱包,保护我的数字资产。
這是真的嗎? 我怎麼能確保我的Trezor錢包不會被黑客攻擊呢?
當談到我們的數位資產的安全時,我們必須採取一切預防措施來確保它們的安全。Trezor錢包是存儲加密貨幣的一個受歡迎的選擇,它聲稱是無法被駭。但它真的能夠信守這個承諾嗎?最近,有報導指出,一些用戶的資金被盜,這使Trezor最近受到了關注。一名威脅行為者成功地突破了Trezor的公司SatoshiLabs設置的安全措施,這次駭客攻擊導致許多無辜的用戶被盜走了大量資金。這次駭客攻擊是怎麼發生的呢?看起來,這次攻擊利用了Trezor錢包固件中的一個漏洞。駭客能夠利用這個漏洞,獲得用戶的私密金鑰,使得他們無需授權即可將資金從錢包轉出。為了避免成為這樣的駭客攻擊受害者,Trezor用戶必須立即採取行動。重要的是要將錢包的固件升級到最新版本。這次升級包括安全補丁,可以解決駭客利用的漏洞。此外,用戶應始終謹慎對待網站……
作為保護我們的數碼資產安全的重要手段,我們必須採取一切必要措施。Trezor錢包是一個廣受歡迎的存儲加密貨幣的選擇,聲稱是無法被駭的。但它真的能夠信守這個承諾嗎?最近,有報導指出,一些客戶被盜走資金。一切源於一名威脅行為者成功突破了SatoshiLabs所設置的安全措施,這場駭客攻擊導致許多客戶的資金被盜。那麼,這次駭客攻擊是怎麼發生的呢?看來,這次攻擊利用了Trezor錢包固件的一個漏洞。駭客利用這個漏洞獲取用戶的私密金鑰,無需授權即可將資金從錢包轉出。為了避免成為這樣的駭客攻擊受害者,Trezor用戶必須盡快採取行動。重要的是將錢包固件升級至最新版本。此次升級包括安全補丁,可修補駭客利用的漏洞。此外,用戶應時刻警惕……
當涉及我們數碼資產的安全時,我們必須採取一切預防措施來確保它們的安全。存儲加密貨幣的一個受歡迎的選擇是Trezor錢包,它聲稱是防黑客的。但它真的能夠實現這個承諾嗎?
近期,Trezor在有報導指出一些用戶的資金被盜後受到了質疑。一切始於一位威脅者成功地突破了Trezor背後公司SatoshiLabs設置的安全措施。這次黑客攻擊導致了大量資金從毫無防備的用戶身上被盜走。
那麼,這次黑客攻擊是如何可能的呢?看來,攻擊利用了Trezor錢包固件中的一個漏洞。黑客們能夠利用這個漏洞並獲得用戶的私鑰,讓他們無需授權就能將資金從錢包轉出。
為了防止成為這樣一次黑客攻擊的受害者,Trezor用戶必須立即採取行動。及時更新錢包的固件至最新版本至關重要。此更新包含了針對黑客利用的漏洞的安全補丁。此外,用戶應該時刻警惕魚陣
當涉及到我們數字資產的安全時,我們必須採取一切預防措施來確保其安全。儲存加密貨幣的一個受歡迎選擇是Trezor錢包,它聲稱是防黑客的。但它真的能夠兌現這個承諾嗎?
近來,Trezor在一些客戶被盜的報告浮出檯面後受到了關注。一切都始於一名威脅行為者成功地破壞了Trezor背後公司SatoshiLabs設置的安全措施。這次駭客事件導致許多毫不知情的客戶喪失大量資金。
那麼,這次駭客事件是如何可能發生的?嗯,看起來駭客利用了Trezor錢包固件中的一個漏洞。駭客們能夠利用這個漏洞並取得使用者的私鑰,進而未經授權從錢包轉移資金。
為了避免成為這樣一次駭客事件的受害者,Trezor用戶必須立即採取行動。將錢包的固件更新至最新版本至關重要。此更新包含安全補丁,以修復駭客利用的漏洞。此外,用戶應時刻小心防範釣魚郵件
針對我們的數位資產安全,我們必須採取一切預防措施來確保其安全。存儲加密貨幣的一個熱門選擇是Trezor錢包,它聲稱是無法破解的。但它是否真的能夠達到這個承諾?
最近,有報導指出,Trezor最近受到了關注,因為一些客戶聲稱他們的資金被盜。這一切始於一名威脅行為者成功侵犯了作為Trezor背後公司的SatoshiLabs設置的安全措施。這次駭客攻擊導致許多不知情的客戶失去了大量資金。
那麼,這次駭客攻擊是如何發生的呢?嗯,這個攻擊似乎利用了Trezor錢包固件中的一個漏洞。駭客能夠利用這個漏洞,並獲得用戶的私鑰,使他們能夠在未經授權的情況下將資金從錢包轉出。
為了防止成為這種駭客攻擊的受害者,Trezor用戶必須立即採取行動。非常重要的是將其錢包的固件升級到最新版本。此次更新包含了解決駭客利用的漏洞的安全補丁。此外,用戶應始終對垂釣攻擊郵件保持警惕。
對於我們的數字資產的安全性,我們必須採取一切預防措施來確保它們的安全。以儲存加密貨幣為主的一個熱門選項是Trezor錢包,聲稱是無法被駭入的。但它真的能實現這個承諾嗎?
究竟Trezor錢包是否可能被駭?這裡有真相嗎?
在保護我們的數碼資產安全方面,我們必須採取一切預防措施。一個常見的選擇是使用Trezor錢包存儲加密貨幣,該錢包聲稱無法被黑客入侵。但它真的能夠履行這個承諾嗎?
近來,Trezor在一些客戶被盜資金的報導出現後受到了質疑。一切都始於一個威脅演員成功地破壞了Trezor背後的SatoshiLabs設置的安全措施。這次黑客攻擊導致許多毫無戒心的客戶失去了大量資金。
那麼,這次黑客攻擊是如何可能的呢?看來黑客是利用Trezor錢包固件的漏洞來實現的。黑客利用這個漏洞獲得了用戶的私鑰,使他們可以在未經授權的情況下從錢包轉賬。
為了防止成為此類黑客攻擊的受害者,Trezor用戶必須立即採取行動。至關重要的是將他們的錢包固件更新到最新版本。此次更新包括了針對黑客利用的漏洞的安全補丁。此外,用戶應始終謹慎對待欺詐攻擊郵件並保護好他們的Trezor錢包。
對於保護我們的數字資產安全,我們必須採取一切預防措施。對於存儲加密貨幣的一個熱門選擇是Trezor錢包,它聲稱是防黑客的。但它真的能擺脫這個承諾嗎?Trezor最近在有報導指出,一些客戶的資金被盜後受到質疑。這一切都始於一名威脅行動者成功闖入Trezor背後的SatoshiLabs制定的安全措施。這種黑客行為導致許多我們的客戶的資金被盜。
那麼,這樣的黑客攻擊怎麼可能發生呢?看來這次黑客攻擊利用了Trezor錢包固件中的一個漏洞。黑客能夠利用這個漏洞並訪問用戶的私密金鑰,並允許他們未經授權即將資金從錢包中轉移出去。為了防止成為這一黑客攻擊的受害者,Trezor用戶必須立即採取行動。更新他們錢包的固件到最新版本是至關重要的。此更新包括解決黑客利用的漏洞的安全補丁。此外,用戶應始終警惕針對Trezor錢包的詐騙攻擊郵件,並保護自己的Trezor錢包。
對於文章內容,Trezor錢包可以被駭客入侵嗎?
對於我們的數碼資產的安全性,我們必須採取一切預防措施確保其安全。一個常見的選擇是使用Trezor錢包來儲存加密貨幣,它聲稱是無法被黑客入侵的。但它真的能夠信守這個承諾嗎?
最近,Trezor在有報導指出一些客戶的資金被盜之後受到了質疑。一切始於一個威脅行為者成功地打破了SatoshiLabs所設的保安措施,這家公司是Trezor背後的公司。這次入侵導致許多不知情的客戶失去了大量資金。
那麼,這次入侵是如何發生的呢?看起來,這次攻擊利用了Trezor錢包固件中的一個漏洞。黑客能夠利用這個漏洞並獲得使用者的私人金鑰,讓他們未經授權地從錢包轉移資金。
為了避免成為這樣入侵的受害者,Trezor使用者必須立即採取行動。他們需要將錢包的固件更新到最新版本。這次升級包含了安全補丁,可以解決被黑客利用的漏洞。此外,使用者應該時刻警惕針對Trezor錢包的釣魚攻擊郵件。
對於我們的數位資產的安全,我們必須採取一切預防措施來確保其安全。Trezor錢包是存儲加密貨幣的一個熱門選擇,聲稱是無法被破解的。但它真的能兌現這個承諾嗎?
對於我們的數位資產的安全性,我們必須採取一切預防措施來確保其安全。存儲加密貨幣的一個流行選擇是Trezor錢包,它聲稱是防黑客的。但它真的能實現這個承諾嗎?
最近,Trezor在一些客戶的資金被盜的報導出現後,受到了關注。一切都開始於一個威脅行為者成功擊破了SatoshiLabs——Trezor公司背後的公司所實施的安全措施。這次駭客事件導致許多毫無戒心的客戶遭受了巨額損失。
那麼,這次駭客攻擊是如何可能的呢?嗯,看起來,這次攻擊利用了Trezor錢包固件中的漏洞。駭客能夠利用這個漏洞並獲得使用者的私鑰,從而未經授權轉移錢包中的資金。
為了防止成為這樣一次駭客攻擊的受害者,Trezor用戶必須立即採取行動。將其錢包的固件更新至最新版本至關重要。這次更新包括解決了駭客利用的漏洞的安全補丁。此外,用戶應始終對釣魚攻擊郵件保持警惕。
對於這篇文章內容有什麼疑問嗎?Trezo 錢包真的可能被駭嗎?
對於這篇文章內容,Trezor 錢包真的可以被駭嗎?
對於這篇文章的內容我有個問題,Trezor Wallet 究竟是否真的無法被駭?文章中提到的最新線上攻擊是怎麼發生的?如何保護我們的數位資產避免受到駭客的攻擊?
當涉及到我們數字資產的安全時,我們必須採取一切預防措施來確保它們的安全。 Trezor錢包是存儲加密貨幣的一個熱門選擇,它聲稱無法被黑客入侵。但它真的能夠達到這個承諾嗎?
就我看來,Trezer錢包似乎無法完全擋住駭客攻擊。最近發生的一次針對Trezer用戶的釣魚攻擊事件讓人感到擔憂。希望SatoshiLabs能儘快加強安全措施,保護用戶的數位資產。
究竟Trezor錢包是否可以被駭客入侵?在這裡找出真相!
在保護我們的數碼資產安全方面,我們必須採取一切預防措施。存儲加密貨幣的一個熱門選項是Trezor錢包,它聲稱不會被駭客入侵。但它真的能夠達到這個承諾嗎?根據最近的報告,Trezor最近受到關注,有報告指稱一些客戶的資金已被盜取。一切始於一名威脅行為者設法突破了SatoshiLabs所設立的安全措施,後者是Trezor背後的公司。這次駭客攻擊導致多數無辜客戶的資金被盜。這次駭客攻擊是如何可能的呢?看來,該攻擊利用了Trezor錢包固件中的漏洞。駭客能夠利用這個漏洞並獲取用戶的私鑰,使他們能夠未經授權地轉移資金出錢包。為防止成為這樣一次駭客攻擊的受害者,Trezor用戶必須立即採取行動。將錢包的固件更新至最新版本至關重要。此更新包括安全補丁,可解決駭客利用的漏洞。此外,用戶應始終警惕被駭客騙取的郵件,並保護他們的Trezor錢包。
數字資產的安全至關重要,我們必須採取一切預防措施來確保其安全。存儲加密貨幣的一個熱門選擇是Trezor錢包,它聲稱是無法被駭。但它真的能夠實現這個承諾嗎?Trezor最近在傳出一些客戶被盜取資金的報導後受到質疑。這一切始於一名威脅參數成功地突破了公司背後的SatoshiLabs設置的安全措施。這次駭客事件導致許多毫無戒心的客戶被盜取了大筆資金。這次駭客行為是如何可能的呢?事實顯示,駭客利用了Trezor錢包固件中的漏洞。駭客能夠利用這個漏洞,並取得用戶的私鑰,從而未經授權地將資金轉出錢包。為了防止成為此類駭客的受害者,Trezor用戶必須立即採取行動。重要的是要將其錢包的固件更新到最新版本。此次更新包含了解決駭客利用的漏洞的安全補丁。此外,用戶應始終慎防釣魚
當涉及我們的數字資產的安全時,我們必須採取一切預防措施以確保它們的安全。 一個常見的存儲加密貨幣的選擇是Trezor錢包,它聲稱是無法被黑客入侵的。但它是否真的能夠履行這個承諾呢?Trezor最近在報導中受到質疑,因為一些客戶報告稱有人洗劫了他們的資金。 一切都始於一名威脅行為者成功突破了SatoshiLabs背後的安全措施,這家公司是Trezor的創建者。 這次黑客入侵導致許多毫不知情的客戶的大量資金被盜。 那麼,這次黑客入侵是如何發生的呢? 好吧,看起來這次攻擊利用了Trezor錢包固件中的漏洞。 黑客能夠利用這個漏洞獲得用戶的私鑰,使他們可以未經授權地從錢包轉移資金。 為了防止成為這樣一次黑客入侵的受害者,Trezor用戶必須立即采取行動。 更新他們的錢包固件至最新版本至關重要。 此更新包括解決黑客利用的漏洞的安全補丁。 此外,用戶應始終警惕偽造的…
對於我們的數碼資產的安全,我們必須採取一切預防措施來確保其安全。存儲加密貨幣的一個受歡迎選擇是Trezor錢包,它聲稱是防黑客的。但它真的能達到這個承諾嗎?
最近,有報導指出,一些Trezor用戶失去了他們的資金,這使得Trezor受到了檢視。一切始於一個威脅行動者成功地突破了Trezor幕後公司SatoshiLabs設立的安全措施。這次黑客攻擊導致大量資金從毫無戒心的客戶那裡被竊取。
那麼,這次黑客攻擊是如何可能的呢?看來,攻擊利用了Trezor錢包固件中的一個漏洞。黑客能夠利用這個漏洞並取得用戶的私人金鑰,使他們未經授權就將資金轉出錢包。
為了防止成為這樣的黑客攻擊受害者,Trezor用戶必須立即採取行動。更新他們錢包的固件到最新版本是至關重要的。這次更新包含了安全補丁,用來修補黑客利用的漏洞。此外,用戶應始終注意釣魚攻擊郵件,並保護好他們的Trezor錢包。
Trezor 近期的安全漏洞是否已經完全修復?更新後還有其他需要注意的安全措施嗎?
我對Trezor錢包的安全性感到徹底失望。聽到黑客能夠利用其韌體的漏洞進行攻擊,我不禁擔心我的資產是否也會受到威脅。即使是頂尖公司如SatoshiLabs,也無法完全保證用戶的安全。希望他們能立刻修補這些漏洞,讓用戶能夠放心使用。
我對於Trezor錢包的安全性感到有些擔憂。雖然它聲稱無法被黑客攻擊,但最近發生的事件讓我開始懷疑這是否是真的。更新固件是必要的,但我還是會更加謹慎,尤其是在接收到釣魚郵件的時候。我希望SatoshiLabs能夠加強安全措施,讓我們的數字資產更安全。
我覺得Trezor錢包雖然聲稱可以防止黑客攻擊,但最近的事件讓我感到擔憂。即使是知名的品牌,總會有漏洞存在。我會特別注意及時更新錢包的固件,並對外部郵件保持警惕,以保障我的數位資產安全。
最近對於Trezor錢包的安全性真的有點擔心。 我一直以為它是絕對安全的,但聽到有客戶在最近的攻擊中資金被盜,讓我開始質疑了。 我會儘快更新我的錢包固件,並保持警惕,避免受到網絡詐騙的影響。
聽說最近有黑客攻擊Trezor錢包,請問這是怎麼發生的?如果我已經使用了Trezor,該怎麼保護我的資金不被盜取呢?
我想知道Trezor最近的固件更新是否真的修補了那些被黑客利用的漏洞?
我一直以來都相信Trezor是一個安全的選擇,但最近的事件讓我感到擔憂。雖然SatoshiLabs聲稱他們的錢包是防黑客的,但如果有漏洞被利用,那到底有多安全呢?我已經立即更新了我的錢包韌體,以確保我的資產不再受到威脅。希望大家都能保持警覺!
就算Trezor聲稱安全無虞,但近期的黑客事件讓我開始懷疑了。用戶應該時時保持警覺,並且定期更新固件,這樣才能有效防範潛在的攻擊。
我覺得Trezor錢包的安全性真是令人擔憂。雖然他們宣稱自己是防駭的,但最近的事件顯示出某些安全漏洞仍然存在。使用數位資產時,我們更應警惕,更新固件及謹防釣魚攻擊是必須的,我希望未來能有更好的保障措施。