In the digital age, keeping your funds secure is crucial. That’s why many people turn to hardware wallets, like the Ledger, to protect their digital assets. But what happens when even these supposedly secure devices get hacked?
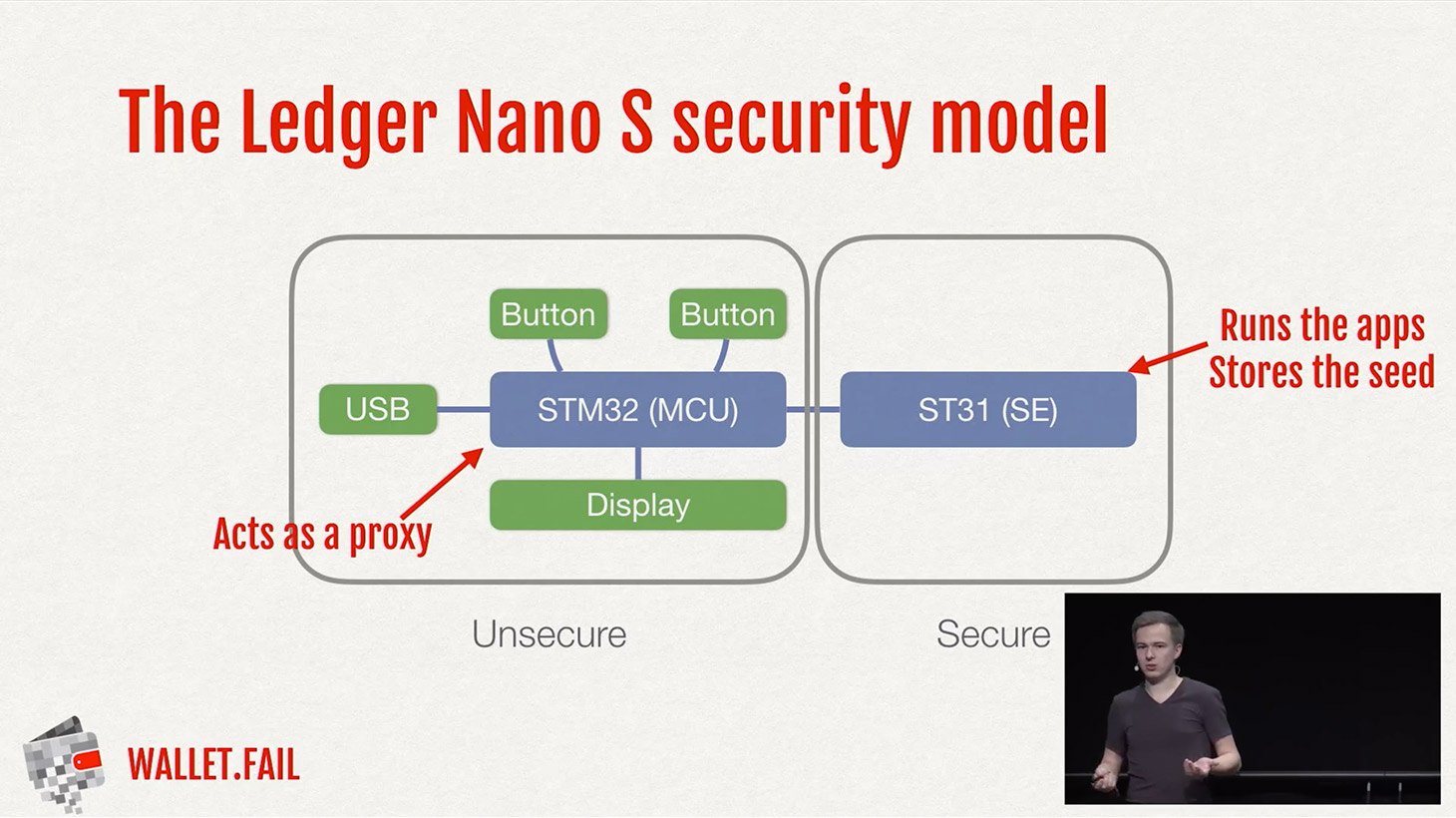
The Ledger hardware wallet is built with the highest level of security in mind. It lets you store your digital currency offline, on a chip that is resistant to various attacks. The chip, called BOLOS, is custom built and has a high level of tampering resistance. This makes it extremely difficult for hackers to access your funds.
However, recent reports have revealed a vulnerability in the Ledger hardware wallet. This vulnerability, known as the “chip + software” vulnerability, allows hackers to gain access to your funds by tampering with both the hardware and the software of the wallet.
So how can you keep your funds safe? One tip is to always make sure you are using the latest version of the Ledger software. The Ledger team regularly releases updates to fix any vulnerabilities that may arise. Additionally, you should also be cautious of any third-party applications or custom chips that you may have installed on your Ledger device. These can potentially weaken the overall security of your wallet.
To protect against attacks, the Ledger wallet also uses a secure operating system called BOLOS. This operating system is designed to withstand various types of attacks, including electromagnetic attacks. It is built with military-grade security in mind, ensuring that your funds are safe.
Overall, while the Ledger hardware wallet is still one of the most secure options available, it is important to stay vigilant and keep up to date with the latest security measures. By following these tips and being aware of any potential vulnerabilities, you can ensure that your digital assets remain secure.
Source: example.com
Contents
- 1 How to Ensure the Security of Your Funds
- 2 Our Military Strength Security Chip Secure Element
- 3 The Custom Operating System BOLOS
- 4 Can A Ledger Wallet Be Hacked?
- 5 Tips to Keep Your Ledger Wallet Safe
- 5.1 1. Use a Secure Hardware Wallet
- 5.2 2. Update Your Wallet Software Regularly
- 5.3 3. Enable Two-Factor Authentication
- 5.4 4. Use a Strong PIN Code
- 5.5 5. Be Cautious of Phishing Attempts
- 5.6 6. Keep Your Recovery Phrase Secure
- 5.7 7. Be Mindful of Physical Attacks
- 5.8 8. Educate Yourself on Security Best Practices
- 6 Understanding the Strength of Your Hardware Wallet
- 7 Protecting Your Hardware Wallet from Vulnerabilities
- 8 Question and answer:
- 9 Video:
How to Ensure the Security of Your Funds
When it comes to protecting your digital funds, security is crucial. With the recent Ledger hardware wallet hack, it is important to take steps to keep your funds safe from any potential vulnerabilities. Here are some tips to ensure the security of your funds:
Choose a Secure Hardware Wallet
One of the best ways to keep your funds secure is by using a hardware wallet. Ledger, for example, offers a range of hardware wallets that are built with the highest level of security in mind. These wallets have a custom operating system called BOLOS which lets you securely manage your applications and funds. By using a hardware wallet, you can protect your funds from any potential software or hardware vulnerabilities.
Look for Tamper-Proof Features
When choosing a hardware wallet, it is important to look for tamper-proof features. Ledger, for instance, uses a military-grade chip that is resistant to physical attacks and tampering. This ensures that your funds are safe even if someone tries to physically access your wallet. Additionally, Ledger’s hardware wallets have built-in secure elements that provide extra protection against various attacks.
Keep Your Software Up to Date
Keeping your hardware wallet’s software up to date is another important step in ensuring the security of your funds. Ledger regularly releases firmware updates that address any potential vulnerabilities and strengthen the overall security of their wallets. By installing these updates, you can make sure that your wallet is protected from the latest threats.
Use Strong Passwords and Enable Two-Factor Authentication
In addition to using a hardware wallet, it is important to use strong passwords and enable two-factor authentication whenever possible. This adds an extra layer of security to your funds and makes it more difficult for hackers to gain access to your wallet. Be sure to choose unique and complex passwords and consider using a password manager to securely store them.
By following these tips and utilizing a secure hardware wallet like Ledger, you can ensure the highest level of security for your digital funds. Remember to stay vigilant and regularly check for any updates or security advisories from your wallet provider. Your funds are only as secure as the measures you take to protect them.
Our Military Strength Security Chip Secure Element
The Ledger hardware wallet is built with a secure element chip, providing military strength security for your digital funds. This secure element chip is a crucial piece of hardware that helps keep your funds safe from tampering and attacks.
What makes this secure element chip so secure? It is designed to withstand various attacks, including physical, software, and electromagnetic attacks. The chip is built to withstand these attacks and ensure the overall security of your wallet.
The secure element chip operates as a secure microcontroller, running its own operating system and software. It lets you make custom applications on top of the secure element, further enhancing the security of your funds.
One of the key features of this secure element chip is its resistance to tampering. It is designed to detect any attempts to tamper with it and will securely wipe the chip if tampering is detected. This ensures that even if your hardware wallet is stolen, your funds remain safe.
With the Ledger hardware wallet and its secure element chip, you can have peace of mind knowing that your digital funds are stored in the highest level of security. The secure element chip is the backbone of Ledger’s security system, keeping your wallets safe and secure.
To further enhance the security of your hardware wallet, Ledger has developed a software called Bolos (Blockchain Open Ledger Operating System). Bolos is a custom operating system that adds an extra layer of security to your wallet by isolating sensitive operations from the main device.
Overall, the military strength security chip secure element in Ledger hardware wallets is what sets them apart from other wallets. It provides the highest level of security for your digital funds, ensuring that they are safe from any vulnerabilities or hacking attempts.
Tips to Keep Your Funds Safe with Ledger Hardware Wallets:
- Always ensure that your Ledger hardware wallet has the latest firmware installed.
- Enable the passphrase feature to add an extra layer of protection to your funds.
- Only purchase your Ledger hardware wallet from the official source to avoid counterfeit devices.
- Regularly check for software updates and install them promptly.
- Keep your recovery seed phrase in a secure location and never share it with anyone.
The Custom Operating System BOLOS
The Custom Operating System BOLOS, also known as Blockchain Open Ledger Operating System, is a crucial element in keeping your funds secure on Ledger hardware wallets. It is a custom-built operating system designed specifically for Ledger devices, providing the highest level of security for your digital assets.
BOLOS is built with the highest security standards in mind and is resistant to attacks such as software tampering and electromagnetic chip vulnerabilities. This makes it extremely difficult for hackers to compromise the security of your wallet and steal your funds.
One of the key features of BOLOS is its ability to keep your applications isolated from each other. Each application runs in its own environment, ensuring that even if one application is compromised, the others remain secure. This adds an extra layer of protection to your funds and reduces the risk of a single vulnerability compromising the overall security of your wallet.
BOLOS also offers a military-grade secure element chip, which further enhances the security of your wallet. This chip is designed to resist various physical and logical attacks, making it extremely difficult for hackers to extract sensitive information or manipulate the software running on your device.
To ensure the highest level of security, it is important to keep your Ledger device’s operating system up to date. Ledger regularly releases firmware updates that address any vulnerabilities and strengthen the security of the device. Make sure to regularly check for updates and install them promptly to keep your funds secure.
In conclusion, the custom operating system BOLOS plays a vital role in securing your digital assets on Ledger hardware wallets. Its built-in security features, isolation of applications, and resistance to attacks make it a reliable and secure choice for storing your funds. By following these tips and keeping your device’s operating system updated, you can have peace of mind knowing that your funds are well protected.
Can A Ledger Wallet Be Hacked?

When it comes to the security of our digital funds, it is crucial to understand how to keep our wallets safe. Ledger hardware wallets are built with the highest security standards in mind, making them one of the most secure options for storing cryptocurrencies.
The Ledger hardware wallet is protected by a secure element chip, which is a tamper-resistant element that lets you securely store and manage your private keys. This chip is designed to withstand various attacks, including physical tampering and electromagnetic attacks.
The Ledger wallet’s software, known as BOLOS (Blockchain Open Ledger Operating System), is also designed with security in mind. BOLOS ensures that the private keys never leave the secure element, providing an additional layer of protection against hacking attempts.
Despite these security measures, no system is 100% hack-proof. While Ledger wallets have not been hacked directly, there have been cases of hackers targeting individuals and using social engineering techniques to gain access to their funds.
To minimize the risk of your Ledger wallet being hacked, it is important to follow some best practices. First, make sure to only purchase your Ledger wallet from the official source to avoid receiving a counterfeit device. Additionally, keep your recovery phrase offline and in a secure location, as this is the key to accessing your funds in case your wallet is lost or stolen.
It is also important to keep your Ledger wallet’s firmware up to date, as firmware updates often include security enhancements and bug fixes. Regularly checking for firmware updates and installing them promptly will help ensure that your wallet is protected against any known vulnerabilities.
In conclusion, while Ledger hardware wallets offer a high level of security, it is important to stay vigilant and take necessary precautions to protect your funds. By following the recommended security practices and keeping your wallet and recovery phrase secure, you can greatly reduce the risk of your Ledger wallet being hacked.
Tips to Keep Your Ledger Wallet Safe
When it comes to securing your funds and keeping your Ledger hardware wallet safe, there are several crucial tips to keep in mind.
1. Use a Secure Hardware Wallet
One of the best ways to ensure the security of your funds is to use a hardware wallet like Ledger. These wallets are built with military-grade security chips that make it extremely difficult for hackers to tamper with or gain access to your digital assets.
2. Update Your Wallet Software Regularly
Keeping your hardware wallet’s software up to date is vital for maintaining the highest level of security. Ledger frequently releases updates that address any vulnerabilities or weaknesses in the system, so make sure to regularly check for and install these updates.
3. Enable Two-Factor Authentication
Adding an extra layer of security to your Ledger wallet is always a good idea. Enable two-factor authentication (2FA) to further protect your funds from unauthorized access. This can be done through the Ledger Live application.
4. Use a Strong PIN Code
Choose a strong PIN code for your Ledger wallet, and avoid using common combinations or easily guessable numbers. A strong PIN code adds an additional layer of security and makes it harder for hackers to gain access to your funds.
5. Be Cautious of Phishing Attempts

Always be careful when entering your wallet information online. Phishing attempts can mimic the Ledger website or application, tricking you into entering your wallet details. Double-check the URL and make sure you are on the official Ledger website before entering any sensitive information.
6. Keep Your Recovery Phrase Secure
Your recovery phrase is a crucial element of your Ledger wallet’s security. Make sure to keep it in a secure location, preferably offline, and never share it with anyone. This recovery phrase is the key to accessing your funds, so protecting it is essential.
7. Be Mindful of Physical Attacks
While Ledger wallets are designed to be secure against digital attacks, physical attacks can still be a vulnerability. Keep your hardware wallet in a safe place and be cautious of any attempts to physically access or tamper with it.
8. Educate Yourself on Security Best Practices
Stay informed and educated about the latest security best practices for using Ledger wallets. Familiarize yourself with the various security features and settings available, and make use of them to enhance the overall security of your digital assets.
By following these tips and implementing the necessary security measures, you can ensure that your Ledger hardware wallet remains secure and your funds are protected from potential threats.
Understanding the Strength of Your Hardware Wallet
When it comes to securing your digital funds, a hardware wallet is one of the highest levels of security you can have. The Ledger hardware wallet, in particular, is built with military-grade security chips that make it extremely difficult to tamper with or hack. In fact, Ledger’s custom operating system, BOLOS, is specifically designed to keep your funds safe.
One of the key elements of the Ledger hardware wallet’s security is its hardware. The chips used in the wallet have a built-in vulnerability that lets them be secure against physical attacks, such as tampering or electromagnetic manipulation. This makes it virtually impossible for hackers to access your funds through traditional hacking methods.
Additionally, the software side of the Ledger hardware wallet is also highly secure. Ledger’s custom operating system, BOLOS, ensures that your wallet’s applications and transactions are protected from any potential vulnerabilities. This means that even if there are software vulnerabilities in other parts of your system, your hardware wallet will remain secure.
So, how can you ensure the overall strength of your hardware wallet? Here are some tips:
- Keep your hardware wallet’s firmware up to date. Ledger regularly releases updates that address any potential security issues.
- Only use official Ledger applications and avoid installing third-party apps on your device.
- Be cautious of phishing attempts. Always double-check the URL and the authenticity of any communication you receive regarding your wallet.
- Keep your recovery phrase offline and in a secure location. This is crucial in case your hardware wallet is lost or stolen.
- Consider using a passphrase in addition to your PIN for added security.
By following these tips and understanding the strength of your hardware wallet, you can be confident that your digital funds are safe and secure. Ledger’s military-grade security chips and custom operating system provide the highest level of protection against potential attacks, making it one of the most secure options for storing and managing your cryptocurrencies.
Protecting Your Hardware Wallet from Vulnerabilities
When it comes to the security of your digital funds, having a hardware wallet is a crucial element. However, it is important to understand that even hardware wallets can have vulnerabilities that can be exploited by hackers. To ensure the highest level of security for your funds, here are some tips on how to protect your hardware wallet:
1. Choose a Secure Hardware Wallet
Not all hardware wallets are created equal. Look for a hardware wallet that is built with military-grade security features and has undergone rigorous testing for vulnerabilities. Ledger, for example, is known for its secure hardware wallets with custom chips specifically designed to protect your funds.
2. Keep Your Operating System and Applications Updated
One of the ways hackers can gain access to your hardware wallet is through vulnerabilities in your operating system or wallet applications. Make sure to regularly update your operating system and wallet applications to patch any security flaws and protect against potential attacks.
3. Protect Against Physical Tampering

Physical tampering is another vulnerability that can compromise the security of your hardware wallet. Look for a wallet that has built-in protections against physical attacks, such as Bolos, which is a secure element chip that prevents unauthorized access to your funds.
4. Be Aware of Electromagnetic Attacks
Electromagnetic attacks can also pose a threat to the security of your hardware wallet. To protect against this vulnerability, choose a wallet that has built-in protections against electromagnetic interference and shielded components.
5. Keep Your Recovery Seed Safe
Your recovery seed is the key to accessing your funds in case your hardware wallet is lost, stolen, or damaged. It is crucial to keep your recovery seed in a secure location, such as a safe or a vault, and never share it with anyone.
6. Be Cautious of Third-Party Software
Avoid using third-party software or applications that claim to enhance the functionality of your hardware wallet. These can introduce vulnerabilities and increase the risk of your funds being hacked. Stick to the official software provided by the hardware wallet manufacturer.
By following these tips, you can significantly enhance the overall strength and security of your hardware wallet, ensuring that your digital funds remain safe from potential attacks or vulnerabilities.
Question and answer:
Can a Ledger hardware wallet be hacked?
Yes, a Ledger hardware wallet can be hacked. Recently, there was a security breach where hackers gained access to the customer database of Ledger, which included personal information such as names, addresses, phone numbers, and email addresses. However, the actual wallets themselves were not compromised. It is important to note that no system is completely foolproof, and there is always a risk of hacking.
What is the strength or vulnerability of a hardware wallet?
The strength of a hardware wallet lies in its robust security features. It uses a secure element chip to store private keys and perform cryptographic operations. This chip is designed to be resistant to physical and software attacks, making it difficult for hackers to gain access to the private keys. However, the vulnerability of a hardware wallet lies in its reliance on software for user interaction. If the software is compromised, it could potentially lead to security breaches.
How does the military strength security chip secure element work?
The military strength security chip secure element used in Ledger hardware wallets is a specialized chip that provides advanced security features. It is designed to resist physical attacks, such as tampering, and uses a secure execution environment to protect sensitive operations. The chip also incorporates cryptographic algorithms to ensure the integrity and confidentiality of the data stored within it. This military-grade security ensures that private keys and other sensitive information are well-protected.
What is the Custom Operating System BOLOS?
The Custom Operating System BOLOS (Blockchain Open Ledger Operating System) is the operating system used in Ledger hardware wallets. It is specifically designed to provide a secure environment for cryptocurrency transactions. BOLOS isolates the execution of sensitive operations, such as private key management, from the main device operating system, reducing the risk of malware and other attacks. This custom operating system adds an extra layer of security to the hardware wallet.
Video:
Did Ledger Really Create A BACKDOOR?!?
Did Ledger Really Create A BACKDOOR?!? by Crypto Tips 1 month ago 14 minutes, 51 seconds 45,135 views
Ledger Live was HACKED. How not to lose all of your cryptocurrency assets. Be Aware of this SCAM.
Ledger Live was HACKED. How not to lose all of your cryptocurrency assets. Be Aware of this SCAM. by Eutropius Bubulcus 5 months ago 3 minutes, 45 seconds 9,097 views
在數字時代,保障資金安全至關重要。這就是為什麼許多人選擇使用硬體錢包,如Ledger,來保護他們的數碼資產的原因。但是,即使這些被認為是安全的設備也被入侵,那要怎麼辦呢?
Ledger硬體錢包是以最高水平的安全性為目標而建造的。它讓您將數字貨幣離線存儲在一個抗擊各種攻擊的芯片上。這個芯片被稱為BOLOS,是定制建造的,具有很高的防竄改性。這使得黑客極難接觸您的資金。
然而,最近的報導揭示了Ledger硬體錢包的脆弱性。這個漏洞被稱為「芯片 + 軟體」漏洞,允許黑客通過篡改錢包的硬體和軟體來獲取您的資金。
那麼,如何保護您的資金安全呢?一個建議是始終確保您使用的是最新版本的Ledger軟體。Ledger團隊定期發布更新以修復可能出現的任何漏洞。此外,您還應該小心注意您可能在您的錢包上安裝的任何第三方應用程式或自定義芯片。
我是很喜欢使用硬件钱包的,因为它提供了更高的安全性保护我的数字资产。然而,当即便这些被称为安全的设备被黑客攻击时,该怎么办呢?还好,来说说Ledger硬件钱包。它采用了最高级别的安全性设计,能够将数字货币离线存储在阻止多种攻击的芯片上。这颗芯片叫做BOLOS,是自定义设计的,并且具有很强的防篡改能力。这使得黑客很难取得您的资产。尽管如此,近期的报道显示Ledger硬件钱包存在一个漏洞。这个漏洞被称为“芯片+软件”漏洞,黑客通过篡改钱包的硬件和软件来获取您的资产。那么,我们如何保障资金的安全呢?一个建议是始终确保您使用的是最新版本的Ledger软件。团队定期发布更新来修复可能出现的漏洞。此外,您还应注意任何第三方应用程序或自定义芯片,这些都可能对资产安全造成风险。
在数字时代,保护资金安全至关重要。这就是为什么很多人会选择像Ledger这样的硬件钱包来保护他们的数字资产。但是,当这些被认为是安全的设备被黑客攻击时又会发生什么呢?
Ledger硬件钱包是以最高级别的安全性为设计理念。它可以让你将数字货币离线存储在一个对各种攻击具有抗性的芯片上。这个名为BOLOS的芯片是定制构建的,并且具有极高的防篡改能力。这使得黑客很难访问您的资金。
然而,最近的报告揭示了Ledger硬件钱包中的一个漏洞。这个漏洞被称为”芯片+软件”漏洞,它允许黑客通过篡改钱包的硬件和软件来获取您的资金。
那么,你该如何保护你的资金安全呢?一个小建议是始终确保你使用的是最新版本的Ledger软件。Ledger团队定期发布更新来修复可能出现的漏洞。此外,您还应该注意任何第三方应用程序或自定义芯片,可能会安装在您的设备上。
在這個數字時代,保護你的資金安全至關重要。這就是為什麼很多人會選擇硬件錢包,像是Ledger,來保護他們的數字資產。但當這些被認為是安全的設備遭到黑客攻擊時會發生什麼呢?
Ledger硬件錢包是在最高安全水平下建造的。它讓你將你的數字貨幣離線存儲在一個抵抗各種攻擊的芯片上。這個名為BOLOS的芯片是定制的,具有高度抗干擾的能力。這使得黑客極其困難地獲取你的資金。
然而,最近的報導揭示了Ledger硬件錢包的一個漏洞。這個漏洞被稱為”芯片+軟件”漏洞,它允許黑客通過對錢包的硬件和軟件進行篡改來獲取你的資金。
那麼如何保護你的資金安全呢?一個提示是始終確保你使用的是最新版本的Ledger軟件。Ledger團隊定期發布更新以修復可能出現的任何漏洞。此外,你還應該對你可能在你的錢包上安裝的任何第三方應用程序或定制芯片保持警惕。
我对硬件钱包的安全性持怀疑态度。尽管它们声称是安全的,但我们还是听到了有关硬件钱包被黑客攻击的报道。这只是加重了我对数字资产安全的担忧。我认为投资者应该追求其他安全措施,而不仅仅依赖硬件钱包。
对于固件的更新没有听说过,这是否意味着硬件钱包不能真正保护我的资金?
這聽起來很可怕!我以為Ledger是安全的,但現在看來,連硬體錢包也不能保護我們的資金了。唉,數字資產的世界真是危機重重,一不小心就可能被駭客攻擊。
这种硬体钱包不是说安全性超强吗?怎么会被黑客攻击呢?
当设备被入侵时,即使是那些被称为安全的硬件钱包也无法保证您的资金安全。我认为随着黑客技术的不断进步,我们需要更加谨慎和警惕。所以,不仅仅是软件升级和安装官方应用,我们还需要自己研究并了解备用防护措施。
有了硬件钱包,可以保证资金的安全性。我一直以来都相信Ledger,但是最近的黑客事件让我很担心。希望他们能尽快解决问题,更新软件,保障用户的资金安全。
在数字时代,保护资金安全至关重要。这就是为什么很多人使用类似Ledger这样的硬件钱包来保护他们的数字资产。但是当即使这些表面上安全的设备也被黑客攻击时会发生什么呢?
Ledger硬件钱包在设计时考虑了最高级别的安全性。它允许您将数字货币离线存储在一个抵御各种攻击的芯片上。这个名为BOLOS的芯片是定制建造的,并具有极高的防篡改能力。这使得黑客极难访问您的资金。
然而,最近的报道揭示了Ledger硬件钱包中的一个漏洞。这个漏洞被称为“芯片+软件”漏洞,允许黑客通过篡改钱包的硬件和软件来获取您的资金。
那么,如何保护您的资金安全呢?一个建议是始终确保使用最新版本的Ledger软件。Ledger团队定期发布更新以修复可能出现的漏洞。此外,您还应谨慎对待您可能在钱包中安装的任何第三方应用程序或定制芯片。
我个人对这个问题有所了解,硬件钱包也不是完全安全的。无论多么安全的硬件钱包,只要涉及到软件,就有潜在的漏洞。所以保证软件的最新版本是非常重要的。此外,也应该将重要的资产分散存储在不同的钱包中,以降低风险。
对于数字货币,安全保护真的非常重要。正因如此,许多人选择使用类似Ledger这样的硬件钱包来保护他们的数字资产。但是,如果即使是这些被认为是安全的设备被黑客攻击,会发生什么呢?
Ledgger硬件钱包是为最高级别的安全而构建的。它可以让您将数字货币离线存储在一个抗击各种攻击的芯片上。这个被称为BOLOS的芯片是定制的,具有很高的防篡改性。这使得黑客几乎无法访问您的资金。
不过,最近的报告揭示了Ledger硬件钱包的一种漏洞。这种漏洞被称为“芯片+软件”漏洞,黑客可以通过篡改钱包的硬件和软件来窃取您的资金。
那么,如何保护您的资金安全呢?一个小建议是始终确保您使用的是最新版本的Ledger软件。Ledger团队会定期发布更新以修复可能出现的漏洞。此外,您还应该注意任何第三方应用程序或自定义芯片,这些可能已经安装在您的设备上。
近來聽到 Ledger 硬件錢包被駭,真是讓人驚慌失措。在數位時代,保護資金安全至關重要。希望 Ledger 團隊能夠盡快解決這個問題,並持續提供更新版本以修復安全漏洞。
在这个数字时代,保护你的资金安全是至关重要的。这就是为什么很多人选择硬件钱包如Ledger来保护他们的数字资产的原因。但是,当即使这些被认为是安全的设备被黑客攻击时,会发生什么呢?
Ledger硬件钱包是以最高安全级别为目标构建的。它允许你将数字货币离线存储在一个对各种攻击具有抗性的芯片上。这个芯片名为BOLOS,是定制建造的,具有高水平的防篡改性。这使得黑客极难访问你的资金。
然而,最近的报道揭示了Ledger硬件钱包的一个漏洞。这个漏洞被称为“芯片+软件”漏洞,允许黑客通过篡改钱包的硬件和软件来获取你的资金。
那么,你如何确保你的资金安全呢?一个提示是始终确保你使用最新版本的Ledger软件。Ledger团队定期发布更新来修复可能出现的任何漏洞。此外,你还应该小心任何你可能在你的钱包上安装的第三方应用程序或自定义芯片。
這篇文章真的很有用!能夠保護我的資金安全對我來說非常重要。看了這篇文章,我終於了解硬體錢包的重要性以及如何保護我的數位資產。我一定會按照文章中的建議,經常更新錢包軟體並注意第三方應用程式或自訂晶片的安全性。
這篇文章真的讓人開眼界!使用Ledger這麼久,沒想到也可能會被黑!那作為使用者,我該怎麼確保我的資金安全呢?
我个人认为Ledger是一种非常安全的硬件钱包,但是即使是看似非常安全的设备也存在被黑客攻破的风险。我们应该经常更新Ledger的软件版本,以修复可能出现的漏洞。此外,对于第三方应用程序或自定义芯片,我们也应保持警惕。
在数字时代,保护好资金安全至关重要。这就是为什么许多人会选择Ledger等硬件钱包来保护他们的数字资产的原因。但是,当这些被认为安全的设备被黑客攻击时会发生什么呢?
Ledger硬件钱包是以最高级别的安全性为目标构建的。它可以让你将数字货币离线存储在一个抗击各种攻击的芯片上。这个芯片名为BOLOS,是定制开发的,具有高度的防篡改能力。这使得黑客极难获取你的资金。
然而,最近的报道揭示了Ledger硬件钱包的一个漏洞。这个漏洞被称为“芯片+软件”漏洞,允许黑客通过篡改钱包的硬件和软件来获取你的资金。
那么,你该如何保护你的资金安全呢?一个建议是始终确保你使用的是最新版本的Ledger软件。Ledger团队定期发布更新,以修复可能出现的任何漏洞。此外,你还应该谨慎对待任何你可能安装在你的设备上的第三方应用程序或定制芯片。
请问我如何确定我所使用的Ledger软件是最新版本的?
這是一個非常重要的問題。在數碼時代,保護我們的資金安全至關重要。即使像Ledger這樣的硬體錢包被黑客攻擊,我們該怎麼辦呢?這真的讓人擔心。現在最好的建議是確保軟件的最新版本,同時要慎重對待任何第三方應用程序或自訂芯片。我們應該要時刻關注安全問題,並且保持警惕。
硬件錢包也不是絕對安全的嗎?這樣的資訊真是令人擔憂。現在什麼都能被駭了,真是要小心。
在數碼時代,保障您的資金安全至關重要。這就是為什麼許多人轉向硬體錢包,如Ledger,來保護他們的數字資產。但當甚至這些被認為是安全的裝置被入侵時會發生甚麼事呢?
Ledger硬體錢包設計時考慮了最高級別的安全性。它讓您在離線狀態下存儲您的數位貨幣,放在一個對各種攻擊具有抵抗力的芯片上。這款名為BOLOS的芯片是定制製造的,具有很高的防篡改能力。這使得駭客非常難以存取您的資金。
然而,最近的報告顯示了Ledger硬體錢包的一個漏洞。這個漏洞稱為“芯片+軟件”漏洞,允許駭客通過篡改錢包的硬體和軟件來存取您的資金。
那麼您如何保護您的資金呢?一個提示是始終確保您使用的是最新版本的Ledger軟件。Ledger團隊定期推出更新,以修復可能出現的任何漏洞。此外,您還應該小心第三方應用程序或您可能已安裝在您的
在數碼時代,保護您的資金至關重要。這就是為什麼許多人選擇使用硬件錢包,如Ledger,來保護他們的數字資產。但當即使這些應該安全的裝置被入侵時會怎樣呢?
Ledger硬件錢包本身就是以最高安全水平為設計原則。它讓您在離線模式下存儲您的數字貨幣,存放在一個抗拒各種攻擊的晶片上。該晶片名為BOLOS,是定制的並具有高度防篡改性,使得駭客極難存取您的資金。
然而,最近的報告披露了Ledger硬件錢包的一個漏洞。這個漏洞被稱為”晶片+軟件”漏洞,它允許駭客通過篡改錢包的硬件和軟件來存取您的資金。
那麼,如何才能確保您的資金安全呢?一個建議是要確保您一直使用最新版本的Ledger軟件。Ledger團隊定期發布更新,來修復任何可能出現的漏洞。此外,您還應注意任何第三方應用程序或自定義晶片,這可能安裝在您的
對於最近 Ledger 硬體錢包被駭事件,如何確保我的資金安全呢?
在數位年代,保護資金安全至關重要。這就是為什麼許多人轉向硬體錢包,像是 Ledger,來保護他們的數位資產。但當即使這些被認為安全的裝置遭到駭客攻擊時會發生什麼?
Ledger 硬體錢包以最高水平的安全性為基礎建立。它讓您將數位貨幣存儲在離線芯片上,這種芯片對各種攻擊有抵抗力。被稱為 BOLOS 的芯片是定制製造的,有很高的防篡改能力。這使得駭客極難接觸您的資金。
但最近的報告揭示了 Ledger 硬體錢包中的一個弱點。這種弱點被稱為「芯片+軟件」漏洞,允許駭客通過篡改錢包的硬體和軟體來訪問您的資金。
那麼怎樣保護您的資金安全?一個建議是總是確保您使用 Ledger 軟體的最新版本。Ledger 團隊定期發布更新,來修復可能出現的任何漏洞。此外,您還應該謹慎對待您可能安裝在您的
數位時代,保障財務安全至關重要。這就是為什麼許多人轉向硬體錢包,如Ledger,以保護他們的數位資產。但當連這些看似安全的設備也被駭客入侵時會怎樣呢?
Ledger硬件錢包以最高級別的安全性為設計基礎。它讓您在線下將數位貨幣存儲在一個對各種攻擊具有抵抗力的芯片上。這個名為BOLOS的芯片是定製的,具有高防篡改能力。這使得駭客幾乎無法接觸您的資金。
然而,最近的報告揭示了Ledger硬件錢包存在的弱點。這個弱點被稱為“芯片+軟件”弱點,允許駭客通過篡改錢包的硬件和軟件來獲取對您資金的存取權。
那麼,如何保護您的資金呢?一個提示是始終確保您正在使用最新版本的Ledger軟件。Ledger團隊定期發布更新,以修復可能出現的任何弱點。此外,您還應該注意您可能在設備上安裝的任何第三方應用程序或自定義芯片。
在數碼時代,保護你的資金至關重要。這就是為什麼許多人選擇硬件錢包,如Ledger,來保護他們的數字資產。但當這些據稱安全的設備甚至被黑客入侵時會發生什麼事呢?
Ledger硬體錢包的建立著眼於最高級別的安全性。它允許您將您的數字貨幣離線存儲在一個抵抗各種攻擊的芯片上。這款名為BOLOS的芯片是定制的,具有很高的防篡改性。這使得黑客極其難以訪問您的資金。
然而,最近的報告揭示了Ledger硬體錢包中的一個漏洞。這個漏洞被稱為「芯片+軟件」漏洞,允許黑客通過篡改錢包的硬件和軟件而存取您的資金。
那麼如何保護你的資金呢?一個提示是始終確保你使用的是最新版本的Ledger軟件。Ledger團隊定期發布更新,以修復可能出現的任何漏洞。此外,您還應該注意任何第三方應用程序或自定義芯片,您可能已經安裝在您的…
這篇文章提到了什麼方法來保護我的Ledger硬體錢包?
在數碼時代,保護自己的資金安全至關重要。因此,許多人選擇使用硬件錢包,像是Ledger,來保護他們的數碼資產。但當即使這些被認為是安全的裝置也被駭客入侵時會發生什麼?
Ledger硬件錢包是建立在最高安全級別的基礎上。它讓你將你的數位貨幣離線存儲在一個抗拒各種攻擊的晶片上。這顆名為BOLOS的晶片是定製建造的,具有很高的防篡改性。這使得駭客幾乎無法存取你的資金。
然而,近期的報告揭示了Ledger硬件錢包中的一個漏洞。這個漏洞被稱為“晶片+軟體”漏洞,能夠讓駭客透過篡改錢包的硬件和軟體而存取你的資金。
那麼該如何保護自己的資金呢?一個貼士是確保你一直使用最新版本的Ledger軟體。Ledger團隊定期發布更新來修復可能出現的任何漏洞。此外,你還應該小心任何可能安裝在你的
在數碼時代,保護資金安全至關重要。這就是為什麼許多人轉向硬體錢包,如Ledger,來保護他們的數字資產。但如果即使這些應該安全的設備也被駭客入侵了,會發生什麼事呢?
Ledger硬體錢包被建造時考慮到了最高級別的安全性。它讓您把數字貨幣存儲在脫機狀態下,放在一個抵抗各種攻擊的芯片上。這個芯片名為BOLOS,是定制建造的,具有高水準的防篡改性。這使得駭客極其困難地進入您的資金。
然而,最近的報告揭示了Ledger硬體錢包的一個漏洞。這個漏洞稱為「芯片+軟件」漏洞,允許駭客通過篡改錢包的硬件和軟件來獲得對您資金的訪問權。
那你該如何保護你的資金呢?一個提示是始終確保您正在使用最新版本的Ledger軟件。Ledger團隊定期發布更新以修復可能出現的任何漏洞。此外,您還應該謹慎對待您可能已經安裝在您的裝置上的任何第三方應用程序或客製化芯片。
點解由 Ledger 硬件錢包都可以俾駭客入侵呢?我應該點樣保護我的數字資產?
在數碼時代中,保護您的資金安全至關重要。這就是為什麼許多人轉向硬體錢包,如 Ledger,來保護他們的數字資產。但即使這些被認為安全的設備被黑客入侵,那又會發生什麼事呢?
Ledger 硬件錢包的建造考慮到了最高水準的安全性。它讓您在線下存儲您的數字貨幣,並且在一個抗擊各種攻擊的晶片上。該晶片名為 BOLOS,是定製建造的,且具有高防篡改性。這使得黑客極其困難地存取您的資金。
然而,最近的報告揭示了 Ledger 硬件錢包中的一個漏洞。這個漏洞被稱為「芯片 + 軟件」漏洞,允許黑客通過操控錢包的硬體和軟件來存取您的資金。
那麼如何保護您的資金安全呢?一個建議是始終確保您正在使用最新版本的 Ledger 軟件。Ledger 團隊定期發布更新版本來修復可能出現的任何漏洞。此外,您還應留意您在錢包上安裝的任何第三方應用程序或自定義晶片。
在數碼時代,保護資金安全至關重要。這就是為什麼許多人轉向硬件錢包,如Ledger,來保護他們的數字資產。但當這些被認為是安全的設備甚至被駭客入侵時,會發生什麼情況呢?Ledger硬件錢包建立在最高安全級別的基礎上。它讓您將數字貨幣離線存儲在一個對各種攻擊具有抵抗力的晶片上。這個名為BOLOS的晶片是定制的,具有很高的耐潑性。這使得駭客極難進入您的資金。然而,最近的報告顯示了Ledger硬件錢包的一個漏洞。這個漏洞被稱為“芯片+軟件”漏洞,允許駭客通過篡改錢包的硬件和軟件來獲取對您資金的訪問權限。那麼你如何保護你的資金呢?其中一個提示是始終確保您在使用最新版本的Ledger軟件。Ledger團隊定期發布更新,以修復可能出現的任何漏洞。此外,您還應該小心任何可能安裝在您的
在數碼時代,保護您的資金安全至關重要。這就是為什麼許多人轉向硬體錢包,如Ledger,來保護他們的數字資產。但當即使這些被聲稱為安全的設備被黑客入侵時會發生什麼?
Ledger硬體錢包是為保安全性而設計的。它允許您將您的數字貨幣儲存在離線芯片上,這個芯片對各種攻擊具有抵抗力。這個名為BOLOS的芯片是定製的,具有很高的防篡改能力。這使得黑客極難進入您的資金。
然而,最近的報告顯示了一個Ledger硬體錢包的漏洞。這個漏洞被稱為“芯片+軟體”漏洞,讓黑客可以通過對錢包的硬體和軟體進行篡改而獲取訪問權限。
那麼如何保護您的資金呢?一個建議是,始終確保您使用的是最新版本的Ledger軟體。Ledger團隊定期發布更新,以修復可能出現的任何漏洞。另外,您還應該小心任何可能安裝在您的設備上的第三方應用程式或定製芯片。
在數字時代,保護您的資金安全至關重要。這就是為什麼許多人轉向硬件錢包,如Ledger,來保護他們的數字資產。但當甚至這些被認為是安全的設備被駭客攻擊時,會發生什麼事呢?
Ledger硬件錢包的建造考慮了最高級別的安全性。它讓您將數字貨幣存儲在離線芯片上,該芯片抵抗各種攻擊。該芯片名為BOLOS,是定制建造的並具有高水平的防篡改性。這使駭客極難存取您的資金。
然而,最近的報告揭示了Ledger硬件錢包中的一個漏洞。這種漏洞被稱為“芯片+軟件”漏洞,允許駭客通過篡改錢包的硬體和軟件來存取您的資金。
那麼如何確保您的資金安全呢?一個提示是始終確保您使用的是最新版本的Ledger軟件。Ledger團隊定期發布更新,以修復可能出現的任何漏洞。此外,您還應該小心任何您可能在您的錢包上安裝的第三方應用程序或自定義芯片。
在數碼時代,保障您的資金安全至關重要。這就是為什麼許多人轉而使用硬體錢包,如Ledger,來保護他們的數字資產。但當即使這些被認為是安全的設備也被駭客攻擊時,會發生什麼事呢?
Ledger硬件錢包是以最高水準的安全性為設計理念。它讓您在一個抗拒各種攻擊的芯片上離線存儲您的數字貨幣。這個名為BOLOS的芯片是定製的,具有很高的防篡改性。這使得駭客極其困難地接觸到您的資金。
然而,最近的報告顯示了Ledger硬件錢包中的一個漏洞。這個漏洞被稱為“芯片+軟件”漏洞,它允許駭客通過篡改錢包的硬件和軟件來獲取您的資金。
那麼你怎樣才能保證資金安全呢?一個建議是始終確保您在使用最新版本的Ledger軟件。Ledger團隊定期發布更新,以修復可能出現的任何漏洞。此外,您也應該注意您可能已安裝在您的硬體錢包上的任何第三方應用程序或定製芯片。
在最新的文章中提到了關於 Ledger 硬件錢包的駭客事件,您認為如何才能確保 Ledger 錢包的安全?
在數碼時代,保障您的資金安全至關重要。這就是為什麼許多人選擇硬體錢包,如Ledger,來保護他們的數字資產。但是,當這些被認為安全的設備甚至被黑客入侵時,會發生什麼事呢?
Ledger硬件錢包是建立在最高安全水平之上的。它讓您將數字貨幣離線存儲在一個對各種攻擊具有抵抗力的芯片上。名為BOLOS的芯片是定製而建,具有很高的防篡改等級。這使得黑客極難存取您的資金。
然而,最近的報告揭示了Ledger硬件錢包中的一個漏洞。這個漏洞被稱為“芯片+軟件”漏洞,它允許黑客通過篡改錢包的硬件和軟件來存取您的資金。
那麼,如何確保您的資金安全呢?一個提示是始終確保您正在使用最新版本的Ledger軟件。Ledger團隊定期發布更新,修復可能出現的任何漏洞。此外,您還應該注意任何可能安裝在您的設備上的第三方應用程序或定製芯片。
在數碼時代,保障資金安全至關重要。這就是為什麼許多人轉向硬件錢包,如Ledger,來保護他們的數字資產。但當甚至這些被認為是安全的設備被黑客入侵時會發生甚麼?
Ledger硬件錢包是為安全性最高水平而建造的。它讓您將您的數字貨幣離線存儲在一個對各種攻擊都抗拒的芯片上。這顆稱為BOLOS的芯片是定制建造的,並具有很高的防篡改性。這使得黑客幾乎無法訪問您的資金。
但近期的報告揭示了Ledger硬件錢包的一個漏洞。這個漏洞被稱為“芯片+軟件”漏洞,允許黑客通過篡改錢包的硬件和軟件來訪問您的資金。
那麼您如何保障您的資金安全呢?一個建議是始終確保您使用最新版本的Ledger軟件。Ledger團隊定期發布更新以修復可能出現的任何漏洞。此外,您還應該小心任何您可能在您的錢包上安裝的第三方應用程序或定制芯片。
在數碼時代,保障您的資金安全至關重要。這就是為什麼許多人轉向硬件錢包,如Ledger,來保護他們的數字資產。但當即使這些被認為是安全的設備被入侵時會發生什麼?Ledger硬件錢包被建造時考慮了最高水平的安全性。它讓您將數字貨幣離線存儲在一個對各種攻擊具有抵抗力的芯片上。被稱為BOLOS的芯片是定制的並具有很高的防破壞性。這使得黑客極難取得您的資金。然而,最近的報告披露了Ledger硬件錢包中的一個漏洞。這個漏洞被稱為“芯片+軟件”漏洞,使黑客可以通過干擾錢包的硬件和軟件來獲取您的資金。那麼,您如何保護您的資金安全呢?一個提示是總是確保您使用最新版本的Ledger軟件。Ledger團隊定期發布更新以修復可能出現的任何漏洞。此外,您還應該小心任何您可能在您的設備上安裝的第三方應用程序或定制芯片。
在數碼時代,保證您的資金安全至關重要。這就是為什麼許多人轉向硬件錢包,例如Ledger,來保護他們的數字資產。但當即使這些應該是安全的設備被駭客入侵時會發生什麼?
Ledger硬件錢包的建構考慮到了最高級的安全性。它讓您將您的數字貨幣離線存儲在一個對各種攻擊具有抵抗力的晶片上。這種晶片稱為BOLOS,是定制設計的,具有很高的防篡改能力。這使得駭客幾乎無法訪問您的資金。
然而,最近的報告揭示了Ledger硬件錢包的一個漏洞。這個漏洞被稱為“晶片+軟件”漏洞,允許駭客通過干擾錢包的硬件和軟件來訪問您的資金。
那麼,您如何保證您的資金安全呢?一個建議是始終確保您正在使用的是最新版本的Ledger軟件。Ledger團隊定期發布更新以修復可能出現的任何漏洞。此外,您還應該謹慎對待您可能安裝在您的硬件錢包上的任何第三方應用程序或定制晶片。
在數位時代,保護自己的資金至關重要。這就是為什麼很多人會選擇像 Ledger 這樣的硬體錢包來保護他們的數位資產。但當這些被認為是安全的設備甚至被駭客入侵時會發生什麼事呢? Ledger 硬體錢包是以最高安全水平為目標打造的。它讓您將您的數位貨幣離線存儲在一塊抗各種攻擊的晶片上。這款晶片名為 BOLOS,是定製化的,具有很高的破壞抵抗能力。這使得駭客極難侵入您的資金。然而,最近的報告揭示了 Ledger 硬體錢包存在漏洞。這個漏洞被稱為「晶片 + 軟體」漏洞,允許駭客通過干擾錢包的硬體和軟體來獲取您的資金。那麼該如何保護您的資金呢?一個提示是確保您始終使用最新版本的 Ledger 軟體。Ledger 團隊定期發布更新,以修復可能出現的漏洞。此外,您還應該注意所安裝在您的
在數碼時代,保護你的資金非常重要。這就是為什麼許多人會轉向硬件錢包,如Ledger,來保護他們的數碼資產。但當這些被認為安全的裝置也被入侵時,會發生什麼事呢?
Ledger硬件錢包是為了提供最高級別的安全性而設計的。它讓你將數碼貨幣離線存儲在一個抗拒各種攻擊的芯片上。這個芯片名為BOLOS,是定製的並具有很高的防篡改性。這使得黑客極難進入你的資金。
然而,最近的報告揭示了Ledger硬件錢包存在的一個弱點。這個弱點被稱為“芯片+軟件”漏洞,允許黑客通過干擾錢包的硬體和軟件來獲取你的資金。
那麼如何保證你的資金安全?一個提示是 總是要確保你使用的是最新版本的Ledger軟件。Ledger團隊定期發布更新,以修復可能出現的任何漏洞。此外,你還應該注意任何你可能在你的…
在數碼時代,保護資金安全至關重要。這就是為什麼許多人轉向硬體錢包,比如Ledger,來保護他們的數碼資產。但是,當即使這些被認為是安全的裝置被入侵時,會發生什麼事呢?Ledger硬體錢包的建造考慮到了最高水平的安全性。它讓您將您的數位貨幣儲存在線下,放在一個對多種攻擊有抵抗力的晶片上。該晶片名為BOLOS,是定制建造的,具有很高程度的防篡改性。這使得駭客極其困難地接觸您的資金。然而,最近的報告揭示了Ledger硬體錢包的一個漏洞。這個漏洞被稱為“晶片+軟體”漏洞,允許駭客通過操作錢包的硬體和軟體來獲取您的資金。那麼,如何保護您的資金呢?一個提示是始終確保您正在使用最新版本的Ledger軟體。Ledger團隊定期發布更新,以修復可能出現的任何漏洞。此外,您還應該注意任何您可能安裝在您的硬體錢包上的第三方應用程式或定制晶片。
隨著Ledger硬體錢包的安全漏洞被曝光,我對數字資產保護的擔憂只會加深。雖然它們的安全性看起來很強,但這次的事件提醒我們,無論什麼技術都不是百分之百安全的。我們必須時刻保持警惕,定期更新軟件,並謹慎使用第三方應用程式。希望Ledger能夠迅速改善這個問題,保障用戶的資金安全。
在這次Ledger硬體錢包的漏洞事件中,您認為最有效的防範措施是什麼?
我對這次 Ledger 硬體錢包被駭的消息感到非常震驚!雖然它的安全設計令人信賴,但這種漏洞讓我感到擔憂。作為一名使用者,我們必須時刻保持警覺,定期更新軟體,並注意不安裝來路不明的應用程式。我希望Ledger能夠迅速解決這個問題,讓我們的資產更安全。
聽到 Ledger 硬體錢包被駭的消息真的讓我很擔心。儘管它的安全衛士聽起來很高級,但網路安全的威脅依然時刻存在。我會確保我的軟體保持最新,並且不會隨意安裝任何第三方應用程式。希望大家都能加倍小心,保護好自己的資產。
最近關於Ledger硬體錢包的漏洞報導讓我很擔心,我想知道我應該如何確認我的錢包是否已被攻擊?
我覺得Ledger硬件錢包的最新漏洞讓我感到非常不安。儘管有軍事級的安全防護,但看來駭客依然能找到方法突破這些防線。為了確保資金安全,我會更小心使用這類設備,並定期更新軟件。不過,我希望Ledger能夠加強其安全性,以防止未來再次出現類似問題。
最近Ledger硬件钱包的安全漏洞令我非常担忧。我一直以为硬件钱包是最安全的选择,如今却感到失望。我希望大家都能保持警惕,定期更新软件,并谨慎使用任何第三方应用。安全至上!
我對最近Ledger硬件錢包被駭的消息感到非常擔憂。雖然它的安全功能看起來很強大,但這次的漏洞讓我重新思考是否真的能完全依賴它來保護我的數字資產。我認為我們每個人都應該更加警惕,定期更新軟件,並避免使用不可靠的第三方應用程式!
我覺得這次Ledger硬體錢包被駭的事件實在令人不安。我一直相信硬體錢包是最安全的選擇,但現在這種漏洞讓我開始懷疑它的可靠性。我會更加注意更新軟體,並避免使用任何不明來源的應用程式,希望未來能有更好的保障措施出現。
最近Ledger硬件錢包的黑客攻擊讓我非常擔心,我想知道有什麼具體的步驟可以進一步加強我的錢包安全性嗎?